Vul. Response Process
Huawei Vulnerability Management Principles
One of our key development strategies is to uphold the continuous construction and full implementation of the "end-to-end global cyber security assurance system." As such, we have established a sustainable and reliable vulnerability management system, which covers policies, organizations, processes, management, technologies, and specifications. Furthermore, we continue to address challenges together with external stakeholders in an open manner.
To clarify our basic position and plans on vulnerabilities, we have proposed five basic principles for vulnerability management:
1. Harm and risk reduction
Reducing or eliminating the harm and security risks caused to customers/users by Huawei product/service vulnerabilities is our vision for vulnerability management and the guideline we follow in vulnerability handling and disclosure.
2. Vulnerability reduction and mitigation
Despite the industry consensus that vulnerabilities are inevitable, we still strive to: (1) Take actions to reduce vulnerabilities in our products and services. (2) Promptly provide risk mitigations to customers/users after vulnerabilities are found in our products and services.
3. Proactive management
Vulnerability issues need to be resolved jointly with upstream and downstream partners throughout the supply chain. We actively identify our vulnerability management responsibilities and requirements (including applicable laws/regulations on business operation, contract requirements, and applicable public standards) and build a system to proactively manage vulnerabilities.
4. Continuous optimization
Threats continuously evolve, meaning that cyber security is a constantly evolving process in which defenders need to constantly innovate. We will continue to optimize our vulnerability management processes and standards, learn from industry standards and best practices, and improve our vulnerability management maturity.
5. Openness and collaboration
We will continue to maintain an open and cooperative attitude to strengthen our connection with the supply chain and the external security ecosystem, including our upstream and downstream partners in the supply chain, security researchers, security companies, and security regulators. In our vulnerability management efforts, we will scale up collaboration with stakeholders and build reliable partnerships.
In compliance with these principles and with industry standards ISO/IEC 30111, ISO/IEC 29147, and ISO/SAE 21434, we have established a robust vulnerability management process. We always uphold our responsibilities and strive to make every effort possible to protect customers and reduce risks caused by vulnerability exploitation.
Vulnerability Handling Process
We are committed to improving the security of our products to fully support the secure operations of customers' networks and services. We have always attached great importance to vulnerability management in product development and maintenance, and have established a robust vulnerability handling process based on ISO/IEC 30111 and ISO/IEC 29147 to improve product security and ensure timely response to vulnerabilities.
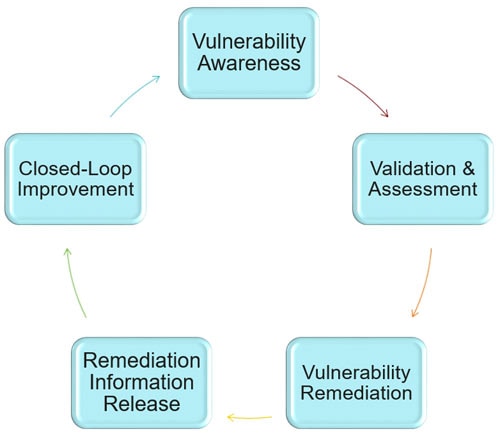
- Vulnerability awareness: Receive and collect suspected vulnerabilities in products.
- Validation & assessment: Confirm the validity and impact scope of suspected vulnerabilities.
- Vulnerability remediation: Develop and implement vulnerability remediation solutions.
- Remediation information release: Release vulnerability remediation information to customers.
- Closed-loop improvement: Make continuous improvement based on customers' comments and practices.
Getting aware of vulnerabilities promptly is a critical prerequisite for timely response. We encourage security researchers, industry organizations, customers, and suppliers to proactively report suspected vulnerabilities to our PSIRT, and require upstream suppliers to promptly report vulnerabilities in deliverables to us. Meanwhile, we proactively monitor well-known public vulnerability databases, open source communities, security websites, and other sources to swiftly detect vulnerabilities related to Huawei products. We manage all suspected vulnerabilities that are known to us and investigate the impact on all product versions that have not reached the end of service & support (EOS). Based on industry best practices, we strongly recommend that customers regularly review the availability of product support to ensure that they are entitled to software updates.
After receiving any suspected vulnerability, our PSIRT will work with the relevant product team to analyze/validate the vulnerability, assess its severity based on its actual impact on products, determine its remediation priority, and develop remediations (including mitigations, patches/versions, and other risk mitigations that can be implemented by customers). Sticking to the principles of harm and risk reduction, we release vulnerability information to stakeholders and help customers assess the actual risks of vulnerabilities to their networks.
When discovering vulnerabilities in the products or services provided by a supplier during product development, delivery, and deployment, we will proactively contact the supplier for vulnerability remediation. For open source software vulnerabilities, we comply with the vulnerability management policies of open source communities, submit suspected vulnerabilities to the communities, promote the communities to release remediations in a timely manner, and actively contribute our remediations to the communities.
Our PSIRT will coordinate with the reporters to handle the vulnerabilities. We may either function as a coordinator or engage a third-party coordination center to transfer vulnerability information to other vendors and standards organizations to promote vulnerability resolution. If the vulnerability involves standard protocols, it is recommended that the reporter notify industry organizations when reporting it to our PSIRT. For example, vulnerabilities related to 3GPP protocols can be reported to the GSMA Coordinated Vulnerability Disclosure (CVD) program.
Adhering to the principle of continuous optimization, we will continuously improve our product security and vulnerability handling process.
Throughout the vulnerability handling process, our PSIRT strictly ensures that vulnerability information is transferred only between relevant handlers. We sincerely request you to keep the information confidential until a complete solution is available to our customers.
We will take necessary and reasonable measures to protect the obtained data based on legal compliance requirements. We will not proactively share or disclose the data to others unless otherwise required by law or by the affected customer.
Vulnerability Severity Rating
We assess the severity of suspected vulnerabilities in our products based on industry standards. Take the Common Vulnerability Scoring System (CVSS) as an example. It is composed of three metric groups: Base, Temporal, and Environmental. We generally provide the base score, and in some cases, provide the temporal score and environmental score of typical scenarios. We encourage end users to assess the actual environmental score based on their network conditions. This score is used as the final vulnerability score in the specific environment to support decision-making on vulnerability mitigation deployment.
In Huawei Cloud, vulnerabilities are prioritized based on the vulnerability exploitation risk assessment result. In Intelligent Automotive Solution (IAS) BU, the severities of vulnerabilities are assessed based on the actual impact on products according to ISO/SAE 21434, and the vulnerability remediation priorities are determined based on their severities.
Different standards are adopted in different industries. We use Security Severity Rating (SSR) as a simpler way to classify vulnerabilities. With SSR, we can classify vulnerabilities as critical, high, medium, low, and informational based on the overall severity score.
Third-Party Software Vulnerability
Considering various scenarios where third-party software/components are integrated into our products in different ways, we will adjust the vulnerability scores of third-party software/components based on specific scenarios to reflect the actual impact of vulnerabilities. For example, if the affected module in the third-party software/component is not called, the vulnerability is considered "not exploitable and has no impact." If a dimension is not covered in the existing assessment system, Huawei is responsible for interpreting the assessment result.
We consider a vulnerability as high profile when the following conditions are all met:
- The CVSS score is 4.0 or above.
- It has aroused wide public attention.
- The vulnerability is likely to be exploited or has already been exploited, or may be exploited in the wild.
For a high-profile third-party vulnerability, we will investigate all product versions that have not reached EOS and release a security notice (SN) within 24 hours after the vulnerability is confirmed as high profile to notify related customers of the handling progress. When a vulnerability mitigation is available, we will release a security advisory (SA) to support customers in risk decision-making and mitigation. For third-party vulnerabilities that are not classified as high profile, we describe them in release notes (RNs).
Vulnerability Bulletins
Publications
We release vulnerability information and remediations in the following publications:
- SA: An SA informs about the remediation, containing information such as the vulnerability severity, service impact, and remediation. Critical and high-risk vulnerabilities directly related with Huawei products and the corresponding remediations are released via SAs. SAs provide the option to download the Common Vulnerability Reporting Framework (CVRF), which is designed to describe vulnerabilities in machine-readable format (XML file) so that affected customers can use it with their tools.
- SN: SNs respond to public security topics (vulnerability related or other topics) on products. Information about the issues whose SSR is informational (for example, an issue discussed in a blog, a discussion list, or other public forums) is released via SNs. In addition, SNs can also be used to notify customers of our vulnerability response progress in certain scenarios, for example, a Huawei product version's vulnerability may arouse wide public concern or has been detected in exploits in the wild.
- RN: RNs contain information about patched vulnerabilities. An RN is part of the deliverables released with a product version/patch, describing vulnerabilities whose SSR is medium or low. RNs also cover the vulnerabilities and the corresponding remediations released via SAs. This is to help customers comprehensively assess vulnerability risks in the version/patch. For private clouds, RNs are contained in the version documents of cloud service products. For consumer products, RNs are contained in routine bulletins.
Channels
Huawei releases SAs and SNs to keep customers informed of vulnerability remediation information. RNs are part of the deliverables released with a product version/patch, and customers can obtain them together with the product version/patch.
Plan
If one or more of the following conditions are met, we will release an SN or SA to facilitate customers in their decision-making on live-network risks.
- The vulnerability SSR is critical or high. We have completed the vulnerability response process and are able to provide a vulnerability remediation solution to support risk mitigation by the customer on its live network.
- Customers are exposed to increasing risks because a vulnerability in a Huawei product version may arouse wide public concern or has been detected in exploits in the wild. In this case, we will accelerate our response, release an SN within 24 hours after confirming the mentioned condition, and keep customers informed of our vulnerability handling progress.
- To minimize global cyber risks, we adhere to the coordinated vulnerability disclosure (CVD) policy when coordinating with third parties for disclosure schedule.
Schedule
To better help customers develop their patch deployment plans and assess risks, we release SAs on a regular basis (on Wednesday). We additionally release SAs outside this schedule in the following cases (not exhaustive):
- We have noticed active exploits of vulnerabilities.
- We have noticed wide public concern about vulnerabilities in our products.
- We collaborate with third parties to disclose vulnerabilities.
Note: For Huawei Cloud, we will disclose vulnerability information and remediation solutions with reference to Huawei Cloud Security White Paper. For consumer products, we usually disclose vulnerability information and remediation solutions in routine bulletins.
How to Obtain Software Updates
Vulnerability management is based on lifecycle milestones of products/software versions. Huawei PSIRT manages the vulnerabilities of all products/versions before they reach the EOS. Vulnerability remediation is provided before the End of Full Support (EOFS). Vulnerabilities whose SSR is critical or high are fixed as appropriate after the EOFS. A product team may use milestones that are not defined in this policy. For details about vulnerability remediation support at other milestones, refer to the specific product documentation.
You can mitigate vulnerability risks by patching or upgrading to a new product/software version according to the contract. You can only obtain and use software versions that have valid (activated on the live network) licenses. Products/Versions that have remediated vulnerabilities do not entitle customers to new software licenses, other software functions/features, or major version upgrades. You can contact Huawei support engineers or TAC to obtain versions or patches:
If you are a customer of Huawei Carrier BG, click here.
If you are a customer of Huawei Enterprise BG, click here.
If you are a customer of Huawei Consumer BG, you can perform online update or click here.
If you are a customer of Huawei Cloud, click here.
If you are a customer of HiSilicon (Shanghai), click here.
If you are a customer of Huawei Enterprise BG, refer to the Product End of Life Policy (https://support.huawei.com/enterprise/en/warranty-policy) of the Enterprise BG to learn details about vulnerability remediation in the product lifecycle. For details about vulnerability remediation capabilities of specific products or software versions, see product lifecycle bulletins at https://support.huawei.com/enterprise/en/bulletins-product.
Disclaimer & Rights Reserved
If this document is available in multiple languages, the Chinese version shall prevail. The policy described in this document does not constitute warranties, commitments, or contract parts. Huawei may adjust it as appropriate.
We reserve the right to change or update this document at any time as necessary to increase transparency or respond more actively. Example updates include:
- Feedback from customers, regulators, the industry, or other stakeholders
- Changes to the overall policy
- Introduction of best practices
As changes to this policy are posted, we will revise the "Update Date" at the bottom of this policy.
Definition
The following table lists the definitions used in this policy.
Updated 2022.1.18

